Information Security Controls Standard (SS-17-001)
Topics:
Information Security Controls Standard
SS-17-001 Information Security Controls
Effective Date: 7/1/2017
Review Date: 12/1/2020
Purpose
In accordance with the Information Security Control Policy, each agency operating within a shared-service environment is responsible for ensuring that applicable NIST 800-53 (rev. 4) security controls are implemented and operated effectively. This standard establishes responsibilities for security controls per application and/or system operating within a shared-services environment.
Standard
Agencies, service providers and integrators will comply with all applicable security controls outlined within the standard in accordance with NIST 800-53. The applicable control families are listed below:
|
Technical Controls |
Operational Controls |
Managerial Controls |
|
AC-Access Control |
AT- Awareness Training |
CA- Security Assessment /Authorization |
|
AU -Audit & Accountability |
CM - Configuration Management |
CP- Contingency Planning |
|
ID - Identification * Authentication |
IR - Incident Response |
PL- Planning |
|
SC - Sys & Communication Protection |
MA - Maintenance |
RA - Risk Assessment |
|
MP- Media Protection |
SA - System & Services Acquisition |
|
|
PE- Physical & Environmental Protection |
||
|
PS- Personnel Security |
||
|
SY- System & Information Integrity |
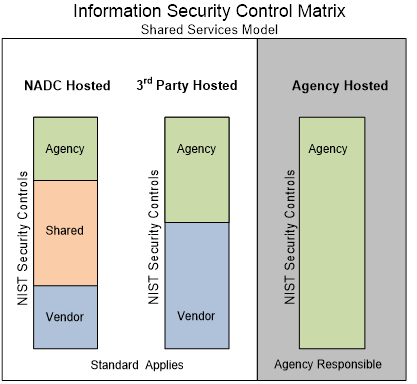
The Information Security Control Matrix (See Appendix A) provides a perspective of shared technical responsibilities for all agencies, service providers, and integrators across the State’s IT enterprise. These responsibilities are based on current NIST best practices and existing enterprise contracts with current service providers and integrators. Appendix A is a tool to demonstrate compliance among State agencies during any and all scheduled IT audits and assessments. If an agency believes that a control is not properly aligned with their operational model, the agency is required to submit a request for an exemption to GTA ([email protected]). Although the agency may not have technical responsibilities for certain NIST 800-53 controls, the agency assumes ultimate accountability for NIST 800-53 compliance requirements. Agencies, service providers and service integrators must comply with all applicable NIST security controls as listed in the matrix below.
Agencies whose IT solutions are hosted, managed and maintained within the NADC or by a 3rd party service provider are required to abide by this standard and the attached security control matrix. This standard does not apply for any systems and/or applications where security is provisioned, implemented and maintained solely by the agency’s staff. If the Information Security Control Standard does not apply, agencies are still required to comply with all other enterprise IT standards.
*Refer to the diagram below as an example

*All other State enterprise IT standards do apply in all three scenarios above.
Definition
Accountable Party: Entity for whom final ownership will be directed for instances of security incidents, breaches or disruptions.
Multisourcing Service Integration (MSI): A company that is responsible for coordinating and overseeing the delivery of technology services to state agencies by multiple service providers.
NIST 800-53: Security and Privacy Controls for Federal Information Systems and Organizations- Provides a catalog of security controls for all U.S. federal information systems except those related to national security.
Responsibility: A group or individual who completes the task.
Service Provider: Organization, business or individual which offers service(s) to others in exchange for payment.
Shared-service Environment: A dedicated unit (including people, processes and technologies) that is structured as a centralized point of service and is focused on defined business functions and providing services for multiple agencies
Appendix A (See Attached File)